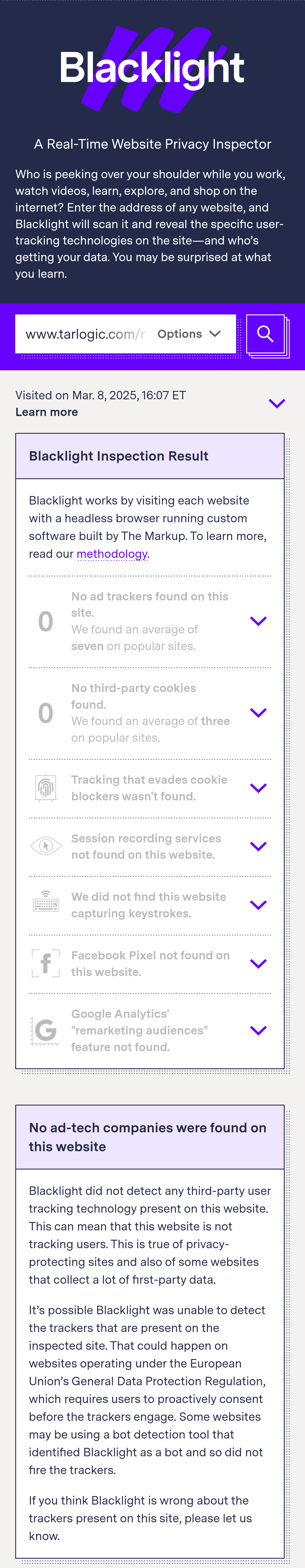
Source Link Privacy.
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.


True, but the ESP32 is used by a lot of devices. This backdoor is pretty huge in scope of devices impacted.
It depends on what the method of attack is. I’m not seeing anything saying that it would be possible to exploit wirelessly, so this could easily be mostly a non-issue.